[2021.7] Share CompTIA CS0-001 practice test questions online preparation material free
CompTIA CS0-001 exam is the most difficult exam to pass. It requires your dedication, hard work, and the most accurate preparation of materials! The latest update CompTIA CS0-001 dumps from Pass4itsure can help you pass your first exam! please click full CompTIA CS0-001 dumps (VCE and PDF, Q&As: 416).
latest update other CompTIA exam practice test
Latest CompTIA CS0-001 actual exam questions for free (update 2021.7)! If you want to read more, this site recommends a complete online blog on CompTIA exam practice questions: downloadzpdf.com. Here, you have everything you need to easily prepare and pass the certification exam.
The updated and valid CompTIA CS0-001 dumps pdf to prepare for the CompTIA CS 0-001 exam:
[free, q1-q13] CompTIA CS0-001 dumps pdf https://drive.google.com/file/d/1WJyy7FP9NwvzKOX4JVYxYxn2xLiUaBxu/view?usp=sharing
Amazing CompTIA CySA+ CS0-001 questions answers (Free part)

QUESTION 1
A security analyst is preparing for the company\\’s upcoming audit. Upon review of the company\\’s latest vulnerability
scan, the security analyst finds the following open issues: Which of the following vulnerabilities should be prioritized for
remediation FIRST?
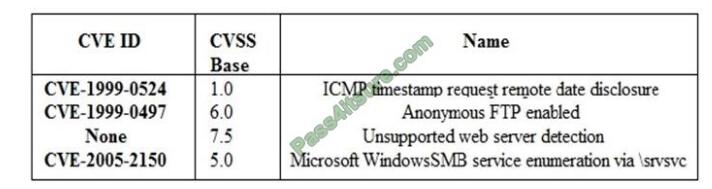
A. ICMP timestamp request remote date disclosure
B. Anonymous FTP enabled
C. Unsupported web server detection
D. Microsoft Windows SMB service enumeration via \srvsvc
Correct Answer: C
QUESTION 2
A nuclear facility manager determined the need to monitor utilization of water within the facility. A startup company just
announced a state-of-the-art solution to address the need for integrating the business and ICS network. The solution
requires a very small agent to be installed on the ICS equipment. Which of the following is the MOST important security
control for the manager to invest in to protect the facility?
A. Run a penetration test on the installed agent.
B. Require that the solution provider make the agent source code available for analysis.
C. Require through guides for administrator and users.
D. Install the agent for a week on a test system and monitor the activities.
Correct Answer: D
QUESTION 3
Which of the following systems or services is MOST likely to exhibit issues stemming from the Heartbleed vulnerability
(Choose two.)
A. SSH daemons
B. Web servers
C. Modbus devices
D. TLS VPN services
E. IPSec VPN concentrators
F. SMB service
Correct Answer: DE
QUESTION 4
Organizational policies require vulnerability remediation on severity 7 or greater within one week. Anything with a
severity less than 7 must be remediated within 30 days. The organization also requires security teams to investigate the
details of a vulnerability before performing any remediation. If the investigation determines the finding is a false positive,
no remediation is performed and the vulnerability scanner configuration is updates to omit the false positive from future
scans:
The organization has three Apache web servers:
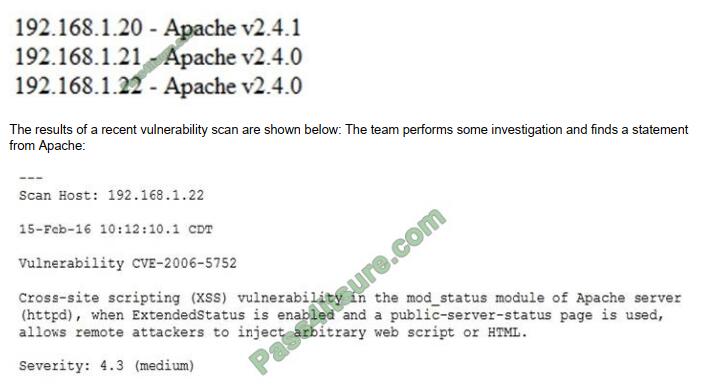
Which of the following actions should the security team perform?
A. Ignore the false positive on 192.168.1.22
B. Remediate 192.168.1.20 within 30 days
C. Remediate 192.168.1.22 within 30 days
D. Investigate the false negative on 192.168.1.20
Correct Answer: C
QUESTION 5
After reviewing the following packet, a cybersecurity analyst has discovered an unauthorized service is running on a
company\\’s computer.
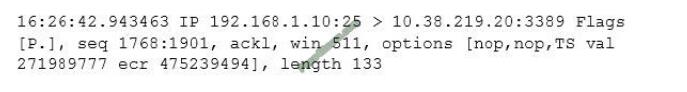
Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not
impact other services?
A. DENY TCP ANY HOST 10.38.219.20 EQ 3389
B. DENY IP HOST 10.38.219.20 ANY EQ 25
C. DENY IP HOST192.168.1.10 HOST 10.38.219.20 EQ 3389
D. DENY TCP ANY HOST 192.168.1.10 EQ 25
Correct Answer: A
QUESTION 6
A centralized tool for organizing security events and managing their response and resolution is known as:
A. SIEM
B. HIPS
C. Syslog
D. Wireshark
Correct Answer: A
QUESTION 7
An analyst suspects a large database that contains customer information and credit card data was exfiltrated to a known
hacker group in a foreign country. Which of the following incident response steps should the analyst take FIRST?
A. Immediately notify law enforcement, as they may be able to help track down the hacker group before customer
information is disseminated.
B. Draft and publish a notice on the company\\’s website about the incident, as PCI regulations require immediate
disclosure in the case of a breach of PII or card data.
C. Isolate the server, restore the database to a time before the vulnerability occurred, and ensure the database is
encrypted.
D. Document and verify all evidence and immediately notify the company\\’s Chief Information Security Officer (CISO) to
better understand the next steps.
Correct Answer: D
QUESTION 8
A security analyst received several service tickets reporting that a company storefront website is not accessible by
internal domain users. However, external users are accessing the website without issue. Which of the following is the
MOST likely reason for this behavior?
A. The FQDN is incorrect.
B. The DNS server is corrupted.
C. The time synchronization server is corrupted.
D. The certificate is expired.
Correct Answer: B
QUESTION 9
The security team has determined that the current incident response resources cannot meet management\\’s objective
to secure a forensic image for all serious security incidents within 24 hours. Which of the following compensating
controls can be used to help meet management\\’s expectations?
A. Separation of duties
B. Scheduled reviews
C. Dual control
D. Outsourcing
Correct Answer: D
QUESTION 10
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized activities.
Which of the following documents should include these details?
A. Acceptable use policy
B. Service level agreement
C. Rules of engagement
D. Memorandum of understanding
E. Master service agreement
Correct Answer: C
QUESTION 11
A threat intelligence feed has posted an alert stating there is a critical vulnerability in the kernel. Unfortunately, the
company\\’s asset inventory is not current. Which of the following techniques would a cybersecurity analyst perform to
find all affected servers within an organization?
A. A manual log review from data sent to syslog
B. An OS fingerprinting scan across all hosts
C. A packet capture of data traversing the server network
D. A service discovery scan on the network
Correct Answer: B
QUESTION 12
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded
and unmanaged HVAC controller, which is used to monitor the company\\’s datacenter:

The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate. Which of the following
should the security administrator implement to harden the system?
A. Patch and restart the unknown service.
B. Segment and firewall the controller\\’s network.
C. Disable the unidentified service on the controller.
D. Implement SNMPv3 to secure communication.
E. Disable TCP/UDP ports 161 through 163.
Correct Answer: A
QUESTION 13
An analyst is observing unusual network traffic from a workstation. The workstation is communicating with a known
malicious site over an encrypted tunnel. A full antivirus scan with an updated antivirus signature file does not show any
sign of infection. Which of the following has occurred on the workstation?
A. Zero-day attack
B. Known malware attack
C. Session hijack
D. Cookie stealing
Correct Answer: A
Reason for selection
Trust Pass4itsure to help you pass the exam 100%!

CompTIA CySA+ CS0-001 exam discount code for free

Refer Pass4itsure for best collection for CompTIA CySA+ CS0-001 exam study material:
- CompTIA CS 0-001 dumps pdf
- CompTIA CS0-001 practice test 1-13 online
- CompTIA CySA+ CS0-001 practice questions form Youtube
Conclusion:
Go ahead and make your success real with 100% valid and real exam material. Choose complete Pass4itsure CS0-001 dumps help, and pass the CS0-001 exam with real and valid questions and answers.
Best of luck for CompTIA CS0-001 exam.