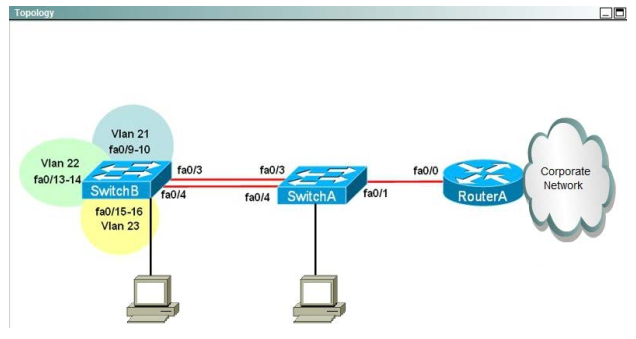
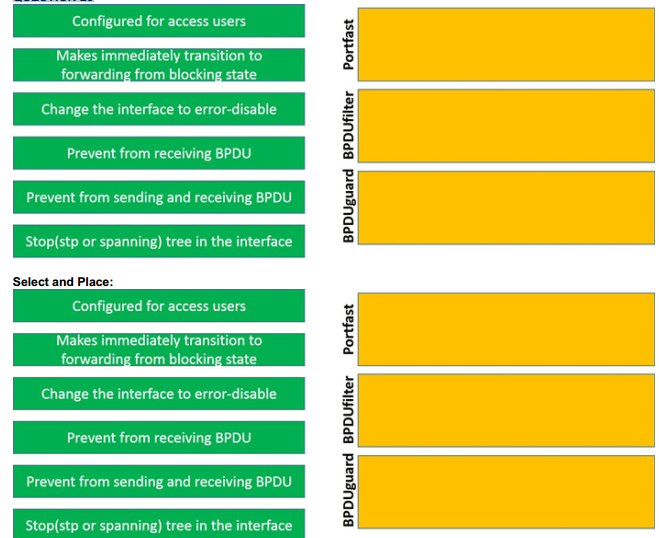
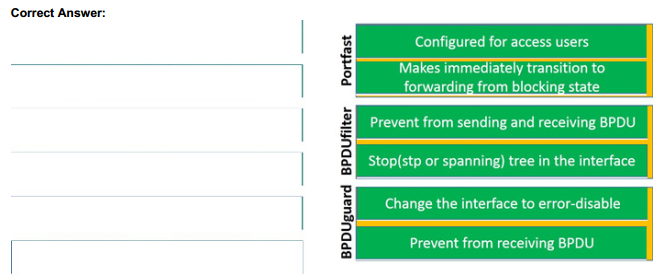
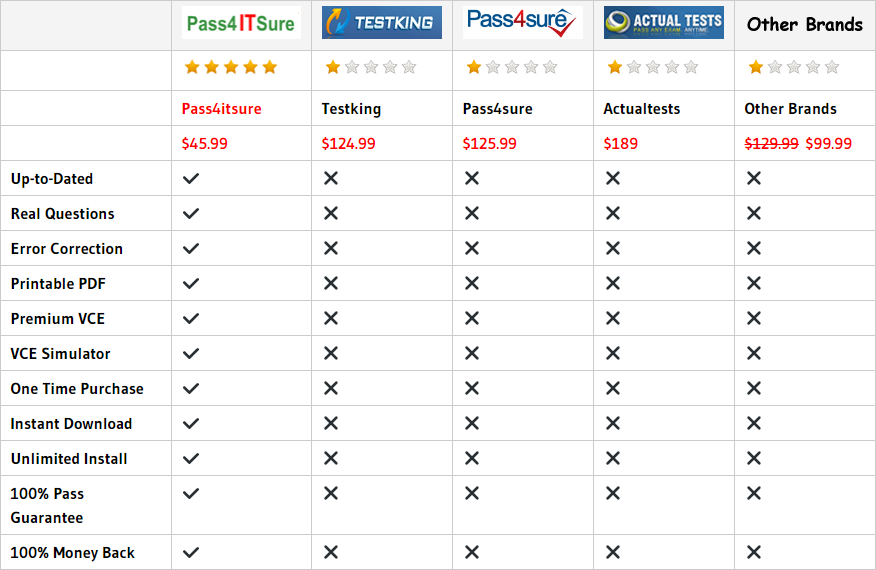
Pass the mb2-718 exam once, the actual effective. Pmtrainingprep share 17 questions and answers for free about
Microsoft Dynamics 365 mb2-718 exam dumps and Microsoft Dynamics 365 mb2-718 PDF online Download.
By the time you see this article, you have made half the success. Next you just have to follow the steps to choose whether to accept us,
free content can help you open the door to learning, if you want to pass the Microsoft Dynamics 365 mb2-718 Exam Once,
you are welcome to choose: https://www.pass4itsure.com/mb2-718.html PDF or VCE.
(Our exam content is provided by pass4itsure Microsoft Exam specialists and all content is
updated throughout the year to ensure 100% valid)
Free Microsoft Dynamics 365 MB2-718 dumps download from Google Drive:
https://drive.google.com/open?id=1YpEQxMo16-a25KfDkkTeeJKkYtz_dLbO
Free Full Microsoft dumps download from Google Drive:
https://drive.google.com/open?id=1VBDzuasBbmByXUKyUaZejR3hFzTke722
Exam MB2-718: Microsoft Dynamics 365 for Customer Service:
https://www.microsoft.com/en-us/learning/exam-mb2-718.aspx
Pass4itsure offers the latest Microsoft Dynamics 365 MB2-718 practice test free of charge (17Q&As)
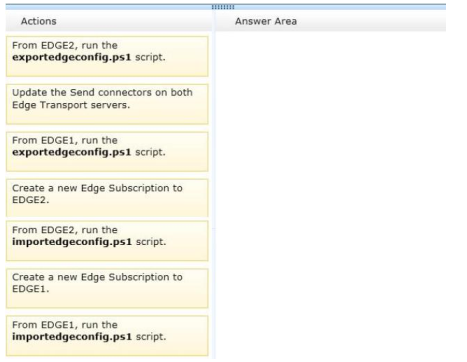
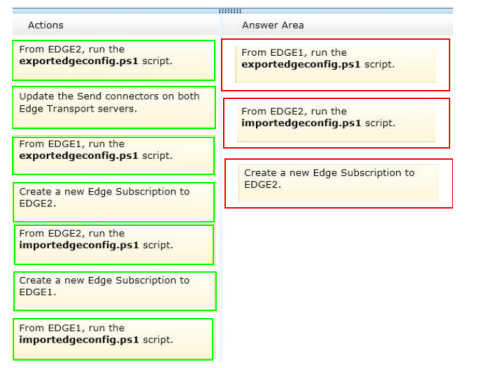
QUESTION 1
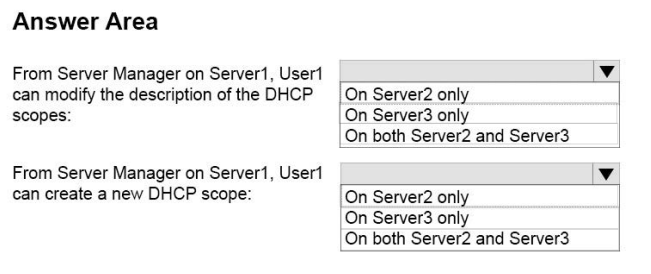
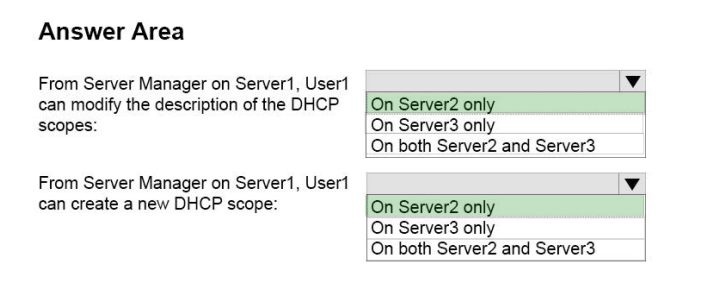
You attempt to delete a queue in Microsoft Dynamics 365. You are not able to delete the queue.
What are two possible reasons why you cannot delete the queue? Each correct answer presents a complete solution.
A. The queue contains a queue item.
B. The queue has a designated email address.
C. The queue is referenced by a routing rule.
D. The queue has a team owner.
Correct Answer: CD
QUESTION 2
You create a service level agreement (SLA) for cases where the case priority is critical. The SLA must display a warning after 15 minutes and fail after 30 minutes.
You create a normal priority case at 16:00. You change the priority to critical at 16:15. If no action is taken, how many minutes will elapse before the SLA fails?
A. 15 minutes
B. 30 minutes
C. 145 minutes
D. 60 minutes
Correct Answer: C
QUESTION 3
Which two actions can you perform by using entitlement channels? Each correct answer presents a complete solution.
A. Specify the number of customers allowed to use each channel ___
B. Restrict users from creating cases by using specified channels.
C. Restrict the number of child cases allowed for each parent case with a specified channel.
D. Specify the number of cases allowed for each channel.
Correct Answer: AB
QUESTION 4
You have a Microsoft Dynamics 365 environment. You implement Field Service. You need to update a work order to indicate that you are traveling to the client.
Which field in the Field Service mobile app should you update?
A. Booking Status
B. Start Time
C. Actual Arrival Time
D. System Status
Correct Answer: D
QUESTION 5
You use the Field Service application.
You need to track users and equipment that are available for scheduling.
Which resource type should you use?
A. Bookable Resource
B. Warehouse Resource
C. Resource Group
D. Web Resource
Correct Answer: D
QUESTION 6
Which two statements regarding the Unified Service Desk (USD) debugger are true? Each correct answer presents a complete solution.
A. Yellow highlights are used to indicate a warning regarding an action call.
B. Red highlights are used to indicate the failure of an event
C. You can view a replacement parameter list.
D. You can run an action call on demand.
Correct Answer: AB
QUESTION 7
Which two statements regarding Microsoft Power BI dashboards are true? Each correct answer presents a complete solution.
A. Visualizations can display up to 5,000 records.
B. You can use Microsoft One Drive for Business as a data connection.
C. You can examine data by using natural language capabilities.
D. You can add up to six visualizations.
Correct Answer: BC
QUESTION 8
You need to search for a specific knowledge base article by number.
Which two options can you use? Each correct answer presents a complete solution.
A. Service Area
B. Relevance Search
C. Categorized Search
D. Article Template Quick Find
Correct Answer: AC
QUESTION 9
You use the interactive service hub for your daily work. You identify a knowledge base article that can assist with an open case for a customer.
You need to send the article to the customer. What should you do?
A. Create a new email record and set the regarding object to the knowledge base article.
B. Use Microsoft Skype for Business to send a link to the customer.
C. Send a link to the customer by using Email a link.
D. Search the knowledge base from within the case, and use the Link Article and Email Content option.
Correct Answer: C
QUESTION 10
A user selects a case from a queue and studies the queue item details for the case. Which two data points are displayed? Each correct answer presents a complete solution.
A. the user who owns the case
B. the time spent working on the case
C. the queue the case is related to
D. the user working on the case
Correct Answer: BD
QUESTION 11
Which queue type is created when you add a user to Dynamics 365?
A. System
B. Personal
C. Escalation
D. Shared
Correct Answer: D
QUESTION 12
You manage a Microsoft Dynamics 365 deployment You need to enable editable grids for an entity. What should you do?
A. Customize the entity.
B. Use the System Customizer tool.
C. Configure the Microsoft Dynamics CRM for Outlook add-in.
D. Modify the system settings.
Correct Answer: A
QUESTION 13
Which three of the following are valid survey response actions?
A. Restart Survey
B. Toggle Visibility
C. Auto-Populate
D. End Survey
E. Chain Survey
Correct Answer: ADE
QUESTION 14
The time period for a goal was not set correctly. You need to ensure that a user can correct the goal. What should you do?
A. Change the manager for the goal.
B. Add a new goal metric.
C. Add a child goal with the correct time period that is owned by the user.
D. Add a parent goal with the correct time period that is owned by the user.
Correct Answer: A
QUESTION 15
You create a Voice of the Customer survey.
You need to configure an automatic response each time a customer completes the survey.
Which feature or component should you use?
A. rule
B. piped data
C. linked question
D. Microsoft Azure Content Delivery Network (CDN)
Correct Answer: A
QUESTION 16
You have the Customer service representative security role. You apply a filter to the active case system view. You need to save the view. What should you do?
A. Create a personal view.
B. Save the filtered view.
C. Pin the view.
D. Use Save As and give the view a new name.
Correct Answer: D
QUESTION 17
You create and activate an entitlement. The start and end dates for the entitlement are in the future. What is the status of the entitlement?
A. Not started
B. On Hold
C. Pending
D. Waiting
Correct Answer: D
Summarize:Pass the mb2-718 exam once, the actual effective. Pmtrainingprep share 17 questions and answers
for free about Microsoft Dynamics 365 mb2-718 exam dumps and Microsoft Dynamics 365 mb2-718 PDF online Download.
Come here to show that you have learned all of our free content, then please choose whether or not to pass the exam easily.
Pass4itsure offers your study in PDF + VCE mode. 100% valid, one pass mb2-718 exam: https://www.pass4itsure.com/mb2-718.html
Free Microsoft Dynamics 365 MB2-718 dumps download from Google Drive:
https://drive.google.com/open?id=1YpEQxMo16-a25KfDkkTeeJKkYtz_dLbO
Free Full Microsoft dumps download from Google Drive:
https://drive.google.com/open?id=1VBDzuasBbmByXUKyUaZejR3hFzTke722
Pass4itsure Promo Code 15% Off
related: http://www.pmtrainingprep.com/new-discount-citrix-1y0-253-dumps-pdf/