[New Updated Questions] Helpful Cisco 010-151 Dumps DCTECH Practice Exam Questions With High Quality Youtube Study
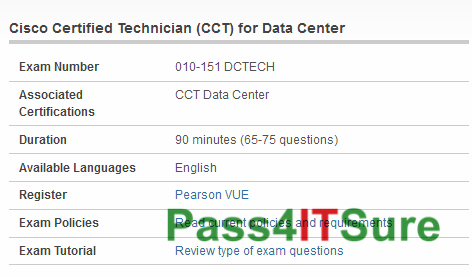
How can I pass the Cisco 010-151 dumps certification exam? The Cisco Certified Technician (CCT) for Data Center (010-151 DCTECH) exam is a 90 minutes (65-75 questions) assessment in pass4itsure that is associated with the CCT Data Center certification. Helpful Cisco 010-151 dumps DCTECH practice exam questions with high quality Youtube study. “Cisco Certified Technician (CCT) for Data Center” is the exam name of Pass4itsure Cisco 010-151 dumps test which designed to help candidates prepare for and pass the Cisco 010-151 exam. Becoming Cisco certified is proving a challenging task for Cisco candidates. Real exam like 010-151 exam are now frequently updating and preparing for this challenge is a tough task. The https://www.pass4itsure.com/010-151.html dumps test is essential and core part of Cisco certification and once you clear the real exam you will be able to get decent job. Many efforts have been made in developing the content and software being used to train you for the 010-151 exam.
[New Updated Cisco 010-151 dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWSno1cV9ERFZGZXc
[New Updated Cisco 210-060 dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWNmlXYjFDT0t3UWc
Share Some Cisco Specialist 010-151 Dumps Exam Questions and Answers Below:
QUESTION 116
Refer to the exhibit.
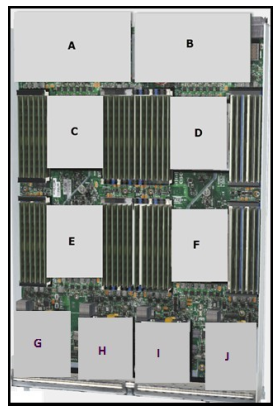
Which item does F represent?
A. HDD 1
B. TFP Module
C. SuperCap Module
D. CPU 2
E. CMOS Battery
010-151 exam Correct Answer: D
QUESTION 117
Refer to the exhibit.
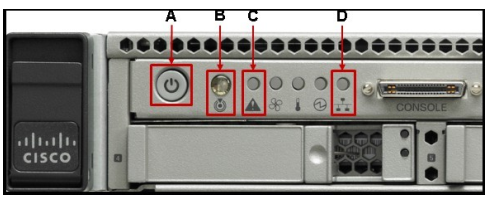
Which statement correctly identifies the front panel LEDs on the Cisco UCS C220 Server?
A. A is power button and power status LED; B is identification button and LED; C is system status LED; D is network link activity LED.
B. A is network link activity LED; B is system status LED; C is power button and power status LED; D is identification button and LED.
C. A is system status LED; B is network link activity LED; C is power button and power status LED; D is identification button and LED.
D. A is network link activity LED; B is system status LED; C is identification button and LED; D is power button and power status LED.
Correct Answer: A
QUESTION 118
Which processor option is supported in the Cisco UCS C420 M3 Server?
A. up to two Intel Xeon E5-4600 series multicore processors
B. up to two Intel Xeon E7-4800 series multicore processors
C. up to four Intel Xeon E5-4600 series multicore processors
D. two or four Intel Xeon E7-8800 series multicore processors
010-151 dumps Correct Answer: C
QUESTION 119
Which two major components does a Cisco Nexus 1000V Series Switch have? (Choose two.)
A. Virtual Fiber Channel Module
B. Virtual Ethernet Module
C. Virtual Supervisor Module
D. Virtual Memory Controller Module
E. Virtual Network Module
Correct Answer: BC
QUESTION 120
Which Cisco Nexus 5000 Series model supports 1/10G BASE-T ports?
A. Cisco Nexus 5548P
B. Cisco Nexus 5548UP
C. Cisco Nexus 5596UP
D. Cisco Nexus 5596T
010-151 pdf Correct Answer: D
QUESTION 121
Which Cisco MDS model supports the most Fibre Channel ports per chassis?
A. MDS 9513
B. MDS 9509
C. MDS 9506
D. MDS 9250i
Correct Answer: A
QUESTION 122
Refer to the exhibit.

Which Cisco MDS chassis supports the 48-Port 16-Gbps Fibre Channel Switching Module?
A. MDS 9509
B. MDS 9513
C. MDS 9710
D. MDS 9506
010-151 vce Correct Answer: C
QUESTION 123
Refer to the exhibit.

What is the name of this rack-mount server?
A. Cisco UCS C220 Rack-Mount Server
B. Cisco UCS C240 Rack-Mount Server
C. Cisco UCS C420 Rack-Mount Server
D. Cisco UCS C460 Rack-Mount Server
Correct Answer: C
QUESTION 124
Which supervisor module is supported by a Cisco Nexus 7700 Series Switch?
A. first-generation supervisor module
B. second-generation supervisor module (Sup2)
C. second-generation supervisor enhanced module (Sup2E)
D. third-generation supervisor enhanced module (Sup3E)
010-151 exam Correct Answer: C
QUESTION NO: 125
The Web resource collection is a security constraint element summarized in the Java Servlet Specification v2.4. Which of the following elements does it include? Each correct answer represents a complete solution. Choose two.
A. HTTP methods
B. Role names
C. Transport guarantees
D. URL patterns
Answer: A,D
Explanation: Web resource collection is a set of URL patterns and HTTP operations that define all resources required to be protected. It is a security constraint element summarized in the Java Servlet Specification v2.4. The Web resource collection includes the following elements: URL patterns HTTP methods Answer: B is incorrect. An authorization constraint includes role names. Answer: C is incorrect. A user data constraint includes transport guarantees.
QUESTION NO: 126
Which of the following activities are performed by the ‘Do’ cycle component of PDCA (plan-do check-act)? Each correct answer represents a complete solution. Choose all that apply.
A. It detects and responds to incidents properly.
B. It determines controls and their objectives.
C. It manages resources that are required to achieve a goal.
D. It performs security awareness training.
E. It operates the selected controls.
010-151 exam Answer: A,C,D,E
Explanation: The ‘Do’ cycle component performs the following activities: It operates the selected controls. It detects and responds to incidents properly. It performs security awareness training. It manages resources that are required to achieve a goal. Answer: B is incorrect. This activity is performed by the ‘Plan’ cycle component of PDCA.
QUESTION NO: 127
Numerous information security standards promote good security practices and define frameworks or systems to structure the analysis and design for managing information security controls. Which of the following are the international information security standards? Each correct answer represents a complete solution. Choose all that apply.
A. AU audit and accountability
B. Human resources security
C. Organization of information security
D. Risk assessment and treatment
Answer: B,C,D
Explanation: Following are the various international information security standards: Risk assessment and treatment: Analysis of the organization’s information security risks Security policy: Management direction Organization of information security: Governance of information security Asset management: Inventory and classification of information assets Human resources security: Security aspects for employees joining, moving, and leaving an organization Physical and environmental security: Protection of the computer facilities Communications and operations management: Management of technical security controls in systems and networks Access control: Restriction of access rights to networks, systems, applications, functions, and data Information systems acquisition, development and maintenance: Building security into applications Information security incident management: Anticipating and responding appropriately to information security breaches Business continuity management: Protecting, maintaining, and recovering business-critical processes and systems Compliance: Ensuring conformance with information security policies, standards, laws, and regulations Answer: A is incorrect. AU audit and accountability is a U.S. Federal Government information security standard.
QUESTION NO: 128
The Data and Analysis Center for Software (DACS) specifies three general principles for software assurance which work as a framework in order to categorize various secure design principles. Which of the following principles and practices does the General Principle 1 include? Each correct answer represents a complete solution. Choose two.
A. Principle of separation of privileges, duties, and roles
B. Assume environment data is not trustworthy
C. Simplify the design
D. Principle of least privilege
010-151 dumps Answer: A,D
Explanation: General Principle 1- Minimize the number of high-consequence targets includes the following principles and practices: Principle of least privilege Principle of separation of privileges, duties, and roles Principle of separation of domains Answer: B is incorrect. Assume environment data is not trustworthy principle is included in the General Principle 2. Answer: C is incorrect. Simplify the design principle is included in the General Principle 3.
QUESTION NO: 129
Fill in the blank with the appropriate security mechanism. is a computer hardware mechanism or programming language construct which handles the occurrence of exceptional events.
A. Exception handling
Answer: A
Explanation: Exception handling is a computer hardware mechanism or programming language construct that handles the occurrence of events. These events occur during the software execution process and interrupt the instruction flow. Exception handling performs the specific activities for managing the exceptional events.
QUESTION NO: 130
In which of the following phases of the DITSCAP process does Security Test and Evaluation (ST&E) occur?
A. Phase 2
B. Phase 4
C. Phase 3
D. Phase 1
010-151 pdf Answer: C
Explanation: Security Test and Evaluation (ST&E) occurs in Phase 3 of the DITSCAP C&A process. Answer: D is incorrect.
The Phase 1 of DITSCAP C&A is known as Definition Phase. The goal of this phase is to define the C&A level of effort, identify the main C&A roles and responsibilities, and create an agreement on the method for implementing the security requirements. The Phase 1 starts with the input of the mission need. This phase comprises three process activities: Document mission need Registration Negotiation Answer: A is incorrect.
The Phase 2 of DITSCAP C&A is known as Verification. The goal of this phase is to obtain a fully integrated system for certification testing and accreditation. This phase takes place between the signing of the initial version of the SSAA and the formal accreditation of the system. This phase verifies security requirements during system development. The process activities of this phase are as follows: Configuring refinement of the SSAA System development Certification analysis Assessment of the Analysis Results Answer: B is incorrect.
The Phase 4 of DITSCAP C&A is known as Post Accreditation. This phase starts after the system has been accredited in the Phase 3. The goal of this phase is to continue to operate and manage the system and to ensure that it will maintain an acceptable level of residual risk. The process activities of this phase are as follows: System operations Security operations Maintenance of the SSAA Change management Compliance validation
QUESTION NO: 131
Which of the following access control models uses a predefined set of access privileges for an object of a system?
A. Role-Based Access Control
B. Discretionary Access Control
C. Policy Access Control
D. Mandatory Access Control
Answer: D
Explanation: Mandatory Access Control (MAC) is a model that uses a predefined set of access privileges for an object of the system. Access to an object is restricted on the basis of the sensitivity of the object and granted through authorization. Sensitivity of an object is defined by the label assigned to it. For example, if a user receives a copy of an object that is marked as “secret”, he cannot grant permission to other users to see this object unless they have the appropriate permission. Answer: B is incorrect. DAC is an access control model. In this model, the data owner has the right to decide who can access the data. Answer: A is incorrect. Role-based access
control (RBAC) is an access control model. In this model, a user can access resources according to his role in the organization. For example, a backup administrator is responsible for taking backups of important data. Therefore, he is only authorized to access this data for backing it up. However, sometimes users with different roles need to access the same resources. This situation can also be handled using the RBAC model. Answer: C is incorrect. There is no such access control model as Policy Access Control.
QUESTION NO: 132
Martha works as a Project Leader for BlueWell Inc. She and her team have developed accounting software. The software was performing well. Recently, the software has been modified. The users of this software are now complaining about the software not working properly. Which of the following actions will she take to test the software?
A. Perform integration testing
B. Perform regression testing
C. Perform unit testing
D. Perform acceptance testing
010-151 vce Answer: B
Explanation: Regression testing can be performed any time when a program needs to be modified either to add a feature or to fix an error. It is a process of repeating Unit testing and Integration testing whenever existing tests need to be performed again along with the new tests. Regression testing is performed to ensure that no existing errors reappear, and no new errors are introduced. Answer: D is incorrect. The acceptance testing is performed on the application before its implementation into the production environment. It is done either by a client or an application specialist to ensure that the software meets the requirement for which it was made. Answer: A is incorrect. Integration testing is a logical extension of unit testing. It is performed to identify the problems that occur when two or more units are combined into a component. During integration testing, a developer combines two units that have already been tested into a component, and tests the interface between the two units. Although integration testing can be performed in various ways, the following three approaches are generally used: The top-down approach The bottom-up approach The umbrella approach Answer: C is incorrect. Unit testing is a type of testing in which each independent unit of an application is tested separately. During unit testing, a developer takes the smallest unit of an application, isolates it from the rest of the application code, and tests it to determine whether it works as expected. Unit testing is performed before integrating these independent units into modules. The most common approach to unit testing requires drivers and stubs to be written. Drivers and stubs are programs. A driver simulates a calling unit, and a stub simulates a called unit.

We have the practice test to prepare you for this. “Cisco Certified Technician (CCT) for Data Center”, also known as 010-151 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. This 010-151 dumps test is an important part of Cisco certification test. Pass4itsure Cisco 010-151 dumps exam questions answers are updated (72 Q&As) are verified by experts. The associated certifications of 010-151 dumps is CCT Data Center. So you want to take advantage of the actual https://www.pass4itsure.com/010-151.html dumps test and save time and money while developing your skills to pass your Cisco Certified Technician (CCT) for Data Center exam? Let us help you climb that ladder of success and pass your 010-151 dumps now!